Windows Container
Table of contents
Windows virtualization
UAC, APP-V, UE-V, Centennial(Desktop bridge), APPX(UWP), MSIX, HYPER-V, Container

[Reference]
- UAC: lucfi.sys
- What is App-V: https://www.tmurgent.com/TmBlog/?p=2489
Container types

Four container types with process based and Hyper-v based:
- Helium – application isolation, based on filesystem and registry virtualization. Used mainly for Windows Store Apps containerization. No security guarantees.
- Argon – user session isolation, with a shared kernel. No security boundary.
- Krypton – hypervisor isolation – a container running on a lightweight Hyper-V VM, which is based on the host kernel. Resistant to kernel attacks.
- Xenon – hypervisor isolation used for hostile multi-tenant hosting. The VM can be based on multiple different kernels. Also known as Hyper-V Containers.
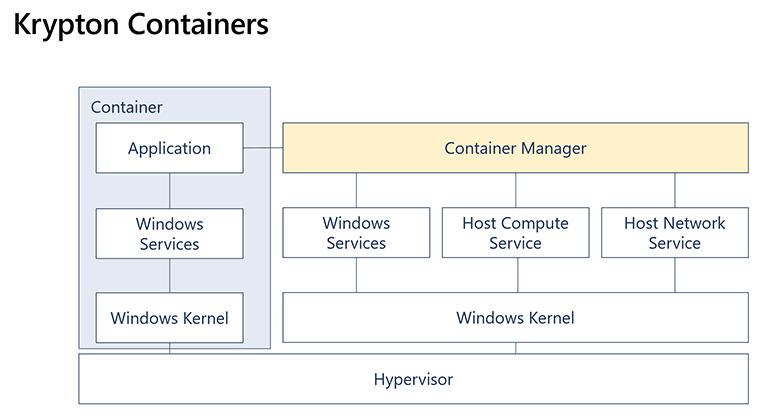
Having created similar lightweight Hyper-V systems for Docker, Windows Defender Application Guard (which has its own kernel) and the Windows Sandbox, the Hyper-V team decided to use the Host Compute Service API in Hyper-V as a platform to allow different Microsoft teams to create their own versions. These Krypton containers don’t have their own copy of the kernel32 module (which is what exposes kernel services to the Win32 environment in Windows) or their own memory allocation and scheduler. They get a read-only version of the same Windows binaries that are already running, so you don’t have to wait for an OS to start up. They direct map in the memory where kernel32 runs in the host, and get memory from the standard Windows memory manager. And their workloads are scheduled by the standard Windows scheduler, so it can freeze threads and suspend processes inside the VM.
That stops the VMs needing significant amounts of memory or slowing the system down, and the connection to the container (which uses the familiar Remote Desktop Protocol) is protected by Control Flow Guard to stop it being abused by an attacker.
[Reference]
- https://devops.com/windows-sandbox-and-hypervisor-based-isolation/
- https://www.techrepublic.com/article/microsoft-windows-what-you-need-to-know-about-whats-coming-next/
- https://www.zdnet.com/article/how-containers-will-transform-windows-10-in-the-next-three-years/
Tech Inside
Windows containers depends on new kernel object called Silos: [https://unit42.paloaltonetworks.com/what-i-learned-from-reverse-engineering-windows-containers/]
Container/Sandbox feasibility study: clear the business purpose
- How to program
- Display performance
- Video & Audio
- No mouse cursor (Touch screen driver)
- VM and Host inter-communication
- diskless or storage encryption
- APP compatible: Chrome + DingDing
[Reference]
- https://github.com/0vercl0k/pywinhv
- https://github.com/ionescu007/Simpleator
- https://github.com/qilingframework/qiling
- http://www.unicorn-engine.org/
The major difference of each feature powdered by Hyper-V:
- Windows Sandbox, Windows Defender Application Guard, System Guard and Advanced Threat Detection, Hyper-V Isolated-Containers, Windows Hypervisor Platform and Windows Subsystem for Linux
- Additionally, applications using Hyper-V, such as Kubernetes for Windows and Docker Desktop, are also being introduced and improved.
Windows Sandbox is built using the same technology we developed to securely operate multi-tenant Azure services like Azure Functions and provides integration with Windows 10 and support for UI based applications.
[Reference]
- https://github.com/ealtili/Blog/blob/master/WindowsSandbox.md
- https://research.checkpoint.com/2021/playing-in-the-windows-sandbox/
The Missing Pieces
Can Windows Sandbox enable organizations to provide an isolated “productivity environment” while further hardening and securing the host OS? In theory, it could, but in practice, unfortunately, it lacks certain capabilities necessary for enterprise environments:
Manageability: It’s hard to deploy and impossible to manage (policies, applications) Windows Sandbox with MDM systems such as Microsoft Intune.
Usability: Windows Sandbox is non-persistent. Applications installed by users or administrators are going to be wiped on reboot. User settings, cookies, and browsing history will not be saved.
OS integration: While users can install risky software inside the container rather than on the host, they are not forced to do so.
Security: While fully isolated in terms of code execution, Windows Sandbox doesn’t provide network isolation. Malware can access and attack other devices accessible by the host, even if behind a Network Access Control (NAC). Software Compatibility: Some applications fail to run or to be installed inside Windows Sandbox.
Hypervisor-based isolation has clear benefits over traditional security methods. By avoiding the cat-and-mouse game, and moving to “mitigation by isolation”, organizations can increase security and productivity, and reduce costs. Once some of the aforementioned gaps are filled, hypervisor-based isolation could become the future of endpoint security.
Applications
Hysolate:https://www.hysolate.com/blog/windows10-technology-for-isolation-workspace-as-a-service/
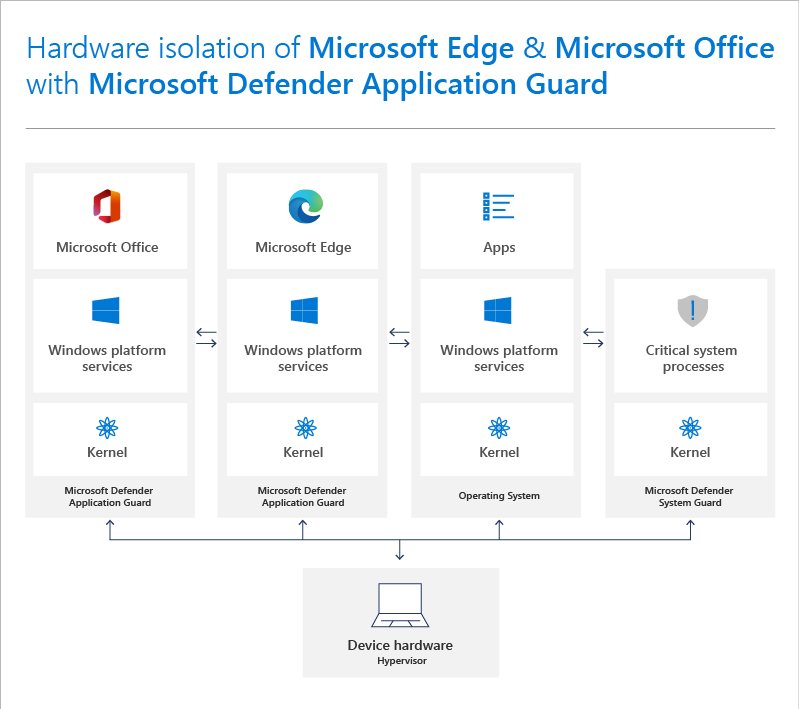
WDAG seems only integrated with edge and office applications. Can not be used generically!!!
[Reference]